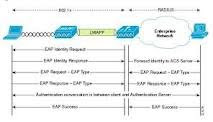
IEEE 802.11i
it requires new encryption key protocols, known as Temporal Key Integrity Protocol (TKIP) and Advanced Encryption Standard (AES). The 802.11i standard was officially ratified by the IEEE in June of 2004, and thereby became part of the 802.11 family of wireless network specifications.
The 802.11i specification offers a level of security sufficient to satisfy most government agencies. However, AES requires a dedicated chip, and this may mean hardware upgrades for most existing Wi-Fi networks. Other features of 802.11i are key caching, which facilitates fast reconnection to the server for users who have temporarily gone offline, and pre-authentication, which allows fast roaming and is ideal for use with advanced applications such as Voice over Internet Protocol (VoIP).
IEEE 802.11r
Uses a 3-tier mention architecture that divides the access network into mobility zones. A mobility zone is defined as the collection of lightweight access points connected to a central management unit, here after referred to as controller. Generally, neighbouring access points covering a certain geographic zone are grouped into a single mobility zone.
IEEE 802.11k
802.11k is a proposed standard for how a wireless local area network (WLAN) should perform channel selection, roaming, and transmit power control (TPC) in order to optimize network performance.
It uses Radio Resource Management which can enable STAs to understand the radio environment in which they exist. The Radio Resource Management service includes measurements that extends the capability, reliability, and the maintainability of WLANs by providing standard measurement s across vendors, and provides the resulting measurement data to upper layers in the communications stack.
IEEE 802.11w
It is a wireless encryption standard relies on 802.11i framework to protect against subtle attacks on wireless LAN (WLAN) management frames .It also defines enhancements such as data integrity, data origin authenticity, replay protection, and data confidentiality.
CMC3P22-P01-1001381A
Thursday, 2 February 2012
Monday, 9 January 2012
Microsoft’s Active Directory Security Feature
Microsoft’s Active Directory overview
Active Directory overview
A directory is a hierarchical structure that stores information about objects on the network. A directory service, such as Active Directory Domain Services (AD DS), provides the methods for storing directory data and making this data available to network users and administrators. For example, AD DS stores information about user accounts, such as names, passwords, phone numbers, and so on, and enables other authorized users on the same network to access this information
Security Features of Microsoft's Active Directory
•Delegated Administration
Allows administrators to assign administrative tasks to other users, while not granting users more power than needed. Delegated administration can be assigned over specific objects or contiguous subtrees of a directory. This is a much more effective method of giving authority over the networks; rather than granting someone the all powerful Domain Administrator permissions, he or she can be given permissions for just those systems and users within a specific subtree. Active Directory supports inheritance, so any new objects inherit the ACL of their container.
•Auditing
Just as you can audit NTFS partitions, objects and containers within Active Directory can be audited. This is a useful way to determine who is attempting to access objects, and whether or not they succeed.
References
http://technet.microsoft.com/en-us/library/cc758436(WS.10).aspx
LDAP Security Feature
Overview of LDAP
Technically, LDAP is just a protocol that defines the method by which directory data is accessed. Necessarily, it also defines and describes how data is represented in the directory service (the Data Model). Finally, it defines how data is loaded into (imported) and saved from (exported) a directory service (using LDIF). LDAP does not define how data is stored or manipulated. Data storage is an 'automagic' process as far as the standard is concerned.
LDAP defines four models which we will now list and discuss - you can then promptly forget them since they bring very little to the understanding of LDAP.
1.Information Model: We tend to use the term Data Model, in our view a more intuitive and understandable term. The Data (or Informational) Model defines how the information or data is represented in an LDAP enabled system - this may, or may NOT, be the way the data is actually stored as explained above.
2.Naming Model: This defines all that 'dc=example,dc=com' stuff that you stumble across in LDAP systems. We stick pretty much to the specifications here because the terms are so widely used.
3.Functional Model: When you read, search, write or modify the LDAP you are using the Functional Model - wow.
4.Security Model: You can control, in a very fine-grained manner, who can do what to what data. This is complex but powerful stuff. We progressively introduce the concepts and have dedicated a specific chapter to it. To begin with - forget security. You can always go back and retro-fit security in LDAP. Where you cannot retro-fit, we reference security implications in the text.
LDAP security features
Network Information Services
When managing a large number of computers it is convenient to store configuration data in a central location rather than maintain separate files on each machine. Thus, DNS quickly replaced large /etc/hostsfiles on the Internet, and a number of more general nameservices were developed to serve more local needs. Sun's YP/NIS is probably the best known, but Hesiod[1] does a similar job and protocol suites such as XNS and NetBIOS also include nameservices of one sort or another.
Network Authentication Service
Authenticating users is one of the more visible aspects of computer security. People are used to providing usernames and passwords when they want to use a machine or other resource.
One approach to authentication in a network is simply to use the NIS to access conventional Unix password hashes and to do the validation locally on the desktop machine. This scheme is commonly used with YP/NIS but it suffers from having to make all password hashes available to all desktop machines. There are shadow-password schemes that prevent `ordinary' users from getting hold of the hash data, but these are fairly easy to bypass when used with a NIS. With access to a collection of password hashes, a cracker can mount a dictionary attack with a good chance of success so it would be better to keep the hashes away from client machines entirely.
References
http://www.skills-1st.co.uk/papers/security-with-ldap-jan-2002/security-with-ldap.html
www.zytrax.com/books/ldap/ch2
Technically, LDAP is just a protocol that defines the method by which directory data is accessed. Necessarily, it also defines and describes how data is represented in the directory service (the Data Model). Finally, it defines how data is loaded into (imported) and saved from (exported) a directory service (using LDIF). LDAP does not define how data is stored or manipulated. Data storage is an 'automagic' process as far as the standard is concerned.
LDAP defines four models which we will now list and discuss - you can then promptly forget them since they bring very little to the understanding of LDAP.
1.Information Model: We tend to use the term Data Model, in our view a more intuitive and understandable term. The Data (or Informational) Model defines how the information or data is represented in an LDAP enabled system - this may, or may NOT, be the way the data is actually stored as explained above.
2.Naming Model: This defines all that 'dc=example,dc=com' stuff that you stumble across in LDAP systems. We stick pretty much to the specifications here because the terms are so widely used.
3.Functional Model: When you read, search, write or modify the LDAP you are using the Functional Model - wow.
4.Security Model: You can control, in a very fine-grained manner, who can do what to what data. This is complex but powerful stuff. We progressively introduce the concepts and have dedicated a specific chapter to it. To begin with - forget security. You can always go back and retro-fit security in LDAP. Where you cannot retro-fit, we reference security implications in the text.
LDAP security features
Network Information Services
When managing a large number of computers it is convenient to store configuration data in a central location rather than maintain separate files on each machine. Thus, DNS quickly replaced large /etc/hostsfiles on the Internet, and a number of more general nameservices were developed to serve more local needs. Sun's YP/NIS is probably the best known, but Hesiod[1] does a similar job and protocol suites such as XNS and NetBIOS also include nameservices of one sort or another.
Network Authentication Service
Authenticating users is one of the more visible aspects of computer security. People are used to providing usernames and passwords when they want to use a machine or other resource.
One approach to authentication in a network is simply to use the NIS to access conventional Unix password hashes and to do the validation locally on the desktop machine. This scheme is commonly used with YP/NIS but it suffers from having to make all password hashes available to all desktop machines. There are shadow-password schemes that prevent `ordinary' users from getting hold of the hash data, but these are fairly easy to bypass when used with a NIS. With access to a collection of password hashes, a cracker can mount a dictionary attack with a good chance of success so it would be better to keep the hashes away from client machines entirely.
References
http://www.skills-1st.co.uk/papers/security-with-ldap-jan-2002/security-with-ldap.html
www.zytrax.com/books/ldap/ch2
X.500 Security Feature
Overview of X.500
The X.500 directory service is a global directory service. Its components cooperate to manage information about objects such as countries, organizations, people, machines, and so on in a worldwide scope. It provides the capability to look up information by name (a white-pages service) and to browse and search for information (a yellow-pages service).
The information is held in a directory information base (DIB). Entries in the DIB are arranged in a tree structure called the directory information tree (DIT). Each entry is a named object and consists of a set of attributes. Each attribute has a defined attribute type and one or more values. The directory schema defines the mandatory and optional attributes for each class of object (called the object class). Each named object may have one or more object classes associated with it.
The X.500 namespace is hierarchical. An entry is unambiguously identified by a distinguished name (DN). A distinguished name is the concatenation of selected attributes from each entry, called the relative distinguished name (RDN), in the tree along a path leading from the root down to the named entry.
X.500 security features
•Authentication (Hashing and asymmetric encryption)
Hashing is the transformation of a message into a usually shorter fixed-length value string that represents the original string using some algorithm. The algorithm must have the characteristic that it is virtually impossible to create a message resulting in a given hash value. A hash value will typically change considerably if just one bit is changed in the original message. This allows for message integrity. If the hash value is attached to the message when transmitted, the receiver can create its own hash value and compare it to the one attached. If different, the message has been changed and should be discarded.
Asymmetric encryption requires the use of an encryption key pair consisting of a private key and a corresponding public key. A message encrypted using one of these keys can only be decrypted using the other key. The owner of the key pair is in the position of the private key. Copies of the public key may be distributed to several parties. A message encrypted by
a public key can only be decrypted by the holder of the private key. This can be used, for example, to encrypt e-mails sent to the holder of the private key
•Decryption
Digital Signatures
A message encrypted by the private key can be decrypted by anyone holding a copy
of the public key. If decryption is possible, only the holder of the private key could have sent this message. This technique is used to create digital signatures.
References
http://docs.oracle.com/javase/jndi/tutorial/ldap/models/x500.html
The X.500 directory service is a global directory service. Its components cooperate to manage information about objects such as countries, organizations, people, machines, and so on in a worldwide scope. It provides the capability to look up information by name (a white-pages service) and to browse and search for information (a yellow-pages service).
The information is held in a directory information base (DIB). Entries in the DIB are arranged in a tree structure called the directory information tree (DIT). Each entry is a named object and consists of a set of attributes. Each attribute has a defined attribute type and one or more values. The directory schema defines the mandatory and optional attributes for each class of object (called the object class). Each named object may have one or more object classes associated with it.
The X.500 namespace is hierarchical. An entry is unambiguously identified by a distinguished name (DN). A distinguished name is the concatenation of selected attributes from each entry, called the relative distinguished name (RDN), in the tree along a path leading from the root down to the named entry.
X.500 security features
•Authentication (Hashing and asymmetric encryption)
Hashing is the transformation of a message into a usually shorter fixed-length value string that represents the original string using some algorithm. The algorithm must have the characteristic that it is virtually impossible to create a message resulting in a given hash value. A hash value will typically change considerably if just one bit is changed in the original message. This allows for message integrity. If the hash value is attached to the message when transmitted, the receiver can create its own hash value and compare it to the one attached. If different, the message has been changed and should be discarded.
Asymmetric encryption requires the use of an encryption key pair consisting of a private key and a corresponding public key. A message encrypted using one of these keys can only be decrypted using the other key. The owner of the key pair is in the position of the private key. Copies of the public key may be distributed to several parties. A message encrypted by
a public key can only be decrypted by the holder of the private key. This can be used, for example, to encrypt e-mails sent to the holder of the private key
•Decryption
Digital Signatures
A message encrypted by the private key can be decrypted by anyone holding a copy
of the public key. If decryption is possible, only the holder of the private key could have sent this message. This technique is used to create digital signatures.
References
http://docs.oracle.com/javase/jndi/tutorial/ldap/models/x500.html
Wednesday, 4 January 2012
GPRS
GPRS features
The technical security offered by GPRS is very similar to that offered by GSM. Identity Confidentiality, Identity authentication, Confidentiality of both the user data and signalling (between the mobile and GPRS serving node-SGSN), and in addition to the GSM standard the security of the GPRS backbone.
GPRS threats
Border Gateway bandwidth saturation – a malicious operator that is connected to the same
GRX (whether or not they’re actually a roaming partner) may have the ability to generate a
sufficient amount of network traffic directed at a Border Gateway such that legitimate
traffic is starved for bandwidth in or out of the PLMN, thus denying roaming access to or
from the network.
DNS Flood – DNS servers on the network can be flooded with either correctly or
malformed DNS queries or other traffic thereby denying subscribers the ability to locate
the proper GGSN to use as an external gateway.
GTP Flood – SGSNs and GGSNs may be flooded with unauthorized GTP traffic that cause
them to spend their CPU cycles processing illegitimate data. This may prevent subscribers
from being able to roam, to pass data out to external networks via the Gi, or from being
able to GPRS attach to the network at all.
„Spoofed GTP PDP Context Delete – An attacker with the appropriate information, can
potentially craft a GTP PDP Context Delete message which will remove the GPRS Tunnel
between the SGSN and GGSN for a subscriber. Crafting other types of network traffic can
learn some of the information that must be known. If an attacker doesn’t care about whom
they are denying service, they can send many PDP Context Delete messages for every
tunnel ID that might be used.
„Bad BGP Routing Information – An attacker who has control of a GRX operators’ routers
or who can inject routing information into a GRX operators’ route tables, can cause an
operator to lose routes for roaming partners thereby denying roaming access to and from
those roaming partners.
„DNS Cache Poisoning – It may be possible for an attacker to forge DNS queries and/or
responses that cause a given user’s APN to resolve to the wrong GGSN or even none at all.
If a long Time To Live (TTL) is given, this can prevent subscribers from being able to pass
data at all.
GPRS threats solutions
Ingress and egress packet filtering – This will help prevent the PLMN from being used as
source to attack other roaming partners. If the mobile operator is connected to more than
one GRX or private roaming peering connections, then this will also help ensure that
spoofed roaming partner traffic cannot arrive on paths where that roaming partner is not
connected.
„Stateful GTP packet filtering – Only allow the traffic required and only from the sources
and destinations of roaming partners. This will prevent other PLMNs connected to the
same GRX from initiating many kinds of attacks. It will also prevent GSNs from having to
process traffic from PLMNs that are not roaming partners as well as illegal or malformed
traffic. Layer 3 and layer 4 stateful inspection is useful because it minimizes the exposure
of the GPRS network, GTP stateful inspection is critical to protect GSNs. A firewall that
supports GTP stateful inspection ensures that GSNs are not processing GTP packets that
are malformed, have illegal headers, or are not of the correct state. This prevents many
types of denial of service attacks and some others such as reconnaissance.
„GTP Traffic Shaping – In order to prevent the shared resources of bandwidth and the
GSN’s processor from being consumed by an attacker or a subscriber, GTP rate limiting
should be implemented. Layer 3 and layer 4 rate limiting should also be implemented to
address Denial of Service (DOS) attacks and ensure that bandwidth is appropriately
apportioned between GTP, BGP, DNS, etc.
„IPSec tunnels between roaming partners – A majority of confidentiality and authentication
issues are addressed by implementing IPSec between you’re the mobile operator PLMN
and that of the roaming partners. Generally, only GTP and DNS traffic should be allowed
over the IPSec tunnel. No traffic should be permitted from roaming partners that does not
arrive on the IPSec tunnel.
„Overbilling Attack Prevention - Juniper’s solution enables the GTP firewall to notify the Gi
firewall of an attack. The Gi firewall is then able to terminate the “hanging” sessions
and/or tunnels, thus cutting off the unwanted traffic. As such, this prevents the GPRS
subscriber from being “overbilled.” Again, this solution is not limited exclusively to the Gp
interface.
The technical security offered by GPRS is very similar to that offered by GSM. Identity Confidentiality, Identity authentication, Confidentiality of both the user data and signalling (between the mobile and GPRS serving node-SGSN), and in addition to the GSM standard the security of the GPRS backbone.
GPRS threats
Border Gateway bandwidth saturation – a malicious operator that is connected to the same
GRX (whether or not they’re actually a roaming partner) may have the ability to generate a
sufficient amount of network traffic directed at a Border Gateway such that legitimate
traffic is starved for bandwidth in or out of the PLMN, thus denying roaming access to or
from the network.
DNS Flood – DNS servers on the network can be flooded with either correctly or
malformed DNS queries or other traffic thereby denying subscribers the ability to locate
the proper GGSN to use as an external gateway.
GTP Flood – SGSNs and GGSNs may be flooded with unauthorized GTP traffic that cause
them to spend their CPU cycles processing illegitimate data. This may prevent subscribers
from being able to roam, to pass data out to external networks via the Gi, or from being
able to GPRS attach to the network at all.
„Spoofed GTP PDP Context Delete – An attacker with the appropriate information, can
potentially craft a GTP PDP Context Delete message which will remove the GPRS Tunnel
between the SGSN and GGSN for a subscriber. Crafting other types of network traffic can
learn some of the information that must be known. If an attacker doesn’t care about whom
they are denying service, they can send many PDP Context Delete messages for every
tunnel ID that might be used.
„Bad BGP Routing Information – An attacker who has control of a GRX operators’ routers
or who can inject routing information into a GRX operators’ route tables, can cause an
operator to lose routes for roaming partners thereby denying roaming access to and from
those roaming partners.
„DNS Cache Poisoning – It may be possible for an attacker to forge DNS queries and/or
responses that cause a given user’s APN to resolve to the wrong GGSN or even none at all.
If a long Time To Live (TTL) is given, this can prevent subscribers from being able to pass
data at all.
GPRS threats solutions
Ingress and egress packet filtering – This will help prevent the PLMN from being used as
source to attack other roaming partners. If the mobile operator is connected to more than
one GRX or private roaming peering connections, then this will also help ensure that
spoofed roaming partner traffic cannot arrive on paths where that roaming partner is not
connected.
„Stateful GTP packet filtering – Only allow the traffic required and only from the sources
and destinations of roaming partners. This will prevent other PLMNs connected to the
same GRX from initiating many kinds of attacks. It will also prevent GSNs from having to
process traffic from PLMNs that are not roaming partners as well as illegal or malformed
traffic. Layer 3 and layer 4 stateful inspection is useful because it minimizes the exposure
of the GPRS network, GTP stateful inspection is critical to protect GSNs. A firewall that
supports GTP stateful inspection ensures that GSNs are not processing GTP packets that
are malformed, have illegal headers, or are not of the correct state. This prevents many
types of denial of service attacks and some others such as reconnaissance.
„GTP Traffic Shaping – In order to prevent the shared resources of bandwidth and the
GSN’s processor from being consumed by an attacker or a subscriber, GTP rate limiting
should be implemented. Layer 3 and layer 4 rate limiting should also be implemented to
address Denial of Service (DOS) attacks and ensure that bandwidth is appropriately
apportioned between GTP, BGP, DNS, etc.
„IPSec tunnels between roaming partners – A majority of confidentiality and authentication
issues are addressed by implementing IPSec between you’re the mobile operator PLMN
and that of the roaming partners. Generally, only GTP and DNS traffic should be allowed
over the IPSec tunnel. No traffic should be permitted from roaming partners that does not
arrive on the IPSec tunnel.
„Overbilling Attack Prevention - Juniper’s solution enables the GTP firewall to notify the Gi
firewall of an attack. The Gi firewall is then able to terminate the “hanging” sessions
and/or tunnels, thus cutting off the unwanted traffic. As such, this prevents the GPRS
subscriber from being “overbilled.” Again, this solution is not limited exclusively to the Gp
interface.
GSM
GSM (Global System for Mobile Communications, originally Groupe Spécial Mobile), is a standard set developed by the European Telecommunications Standards Institute (ETSI) to describe technologies for second generation (2G) digital cellular networks.
GSM features
Key management is independent of equipment it allows the subscribers to be able change handsets without compromising security.
Subscriber identity protection so that it will not be easy to identify the user of the system intercepting a user data.
Detection of compromised equipment it is a detection mechanism whether a mobile device was compromised or not.
Subscriber authentication so that the operator knows for billing purposes who is using the system.
Signaling and user data protecting allows data channels to be protected over the radio path.
GSM threats
Eavesdropping - The capability of an intruder to intercept traffic and signaling information associated to other users. The required equipment is a modified mobile phone.
Impersonation of a user - This is the capability of sending rogue data and/or signaling messages to the network with the intent of making them appear from another user. This again only requires a modified mobile phone.
Impersonation of the network - This is the capability of sending rogue data and/or signaling messages to another user with the intent of making them appear from a genuine network. This
requires a modified BTS.
MITM – Man-In-The-Middle - This is the capability of an attacker to put itself between the network and the legitimate user in order to eavesdrop, modify, delete, re-order, re-play and spoof signaling data between the two parties. This requires a modified BTS in conjunction with a modified mobile phone.
Network Authentication Compromise - The intruder possesses a compromised authentication
vector (challenge-response pairs, cipher keys, integrity key, etc)
GSM threats solution
The GSM security design is weak to the extend that not much improvements could be done to fight against these threats. As communication is done through wireless, (which means that the transmission and reception of messages is conveyed through the air) there are security limitations in mobile communication stem. One of the precaution is anonymity. It helps to make it difficult to identify the user of the system. Anonymity is provided by the use of temporary identifiers. When a new GSM subscriber switches on his/her mobile device for the first time, the real identity which is also known as the International Mobile User/Subscriber Identity (IMUI/IMSI) is used and a Temporary Mobile User/Subscriber Identity (TMUI/TMSI) is then issued to this subscriber. From then on, the temporary identifier is used. The only way of determining the temporary identity being used is by tracking the user. Therefore, the use of TMUI, prevents the recognition of a GSM user by a potential eavesdropper or hacker.
Subscribe to:
Comments (Atom)